All who are dedicated to this IT security, know that there are key tools, especially when making a web pentesting. One of these key tools is the Burp Suite.
However, there are many versions online, and one of the most famous is that of Larry Lau. This version has been controversial, since many doubted the legitimacy of it. This post is not intended to "hack" version of Burp Suite pro, but BurpLoader deobfuscate, decompile, and verify whether or not the existence of malware into the jar file. It has carried out an analysis to Burploader.jar version version 1.6.38.
Once understood the purpose of this post, let's get to work.
However, there are many versions online, and one of the most famous is that of Larry Lau. This version has been controversial, since many doubted the legitimacy of it. This post is not intended to "hack" version of Burp Suite pro, but BurpLoader deobfuscate, decompile, and verify whether or not the existence of malware into the jar file. It has carried out an analysis to Burploader.jar version version 1.6.38.
Once understood the purpose of this post, let's get to work.
The first step is to extract the .jar file class, the BurpLoader, for this will open the .jar file compressor for example WinRar. After removing the .class will proceed to visualize the code to address the problem in the best way possible. We will use the jdecompiler and the .jar file decompiler Burp As shown in the following image we are only able to see the bytecode:
As you can see in the picture above, we can not see the original source code, but you can see the bytecode. So now we need some bytecode decompiler to find out exactly what makes this source code. The code can be recompiled with Eclipse, however I have used a simpler tool called Procyon-decompiler. Procyon run and you look at the part of the obfuscated bytecode ldc(load constant):
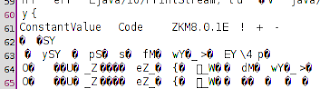
As was seen in the picture above, the ldc is obfuscated. It should then proceed to find out what was the algorithm I use Larry Lau to obfuscate the code, so it can use jedit, obtaining the following results (BurpLoader.class):
Therefore we conclude that the algorithm used is ZKM8.0.1E (http://www.zelix.com/). To deobfuscate this code to need the 5 digit key that can be found very easily with jedit, between others.
Now we need some software that embeds the option to deobfuscate code with ZKM, we disclaim by DirtyJoe, software for Windows.
I do not think it necessary to go into details, once you have the .class deobfuscated must return to the first steps in order to decompile this class. Getting the license using Larry Lau in his Loaders. But it was impossible to determine the existence of malware, since we could not compile the decompiled .java above, since we lacked dependence burp_extras.jar





Great post!
ReplyDelete0Xd0M7: Analizing Burploader.Jar (Larry Lau Version) >>>>> Download Now
Delete>>>>> Download Full
0Xd0M7: Analizing Burploader.Jar (Larry Lau Version) >>>>> Download LINK
>>>>> Download Now
0Xd0M7: Analizing Burploader.Jar (Larry Lau Version) >>>>> Download Full
>>>>> Download LINK hx
Thank You!
ReplyDeleteGood Method, but nice try.
ReplyDeleteThank you.!!
ReplyDelete0Xd0M7: Analizing Burploader.Jar (Larry Lau Version) >>>>> Download Now
ReplyDelete>>>>> Download Full
0Xd0M7: Analizing Burploader.Jar (Larry Lau Version) >>>>> Download LINK
>>>>> Download Now
0Xd0M7: Analizing Burploader.Jar (Larry Lau Version) >>>>> Download Full
>>>>> Download LINK YB